Emails in your inbox now (hopefully) rarely begin with “I am the next heir to the throne in Nigeria…”
That doesn’t mean email scamming has died down — as a matter of fact, even the emails from Nigerian heirs looking to send money to long-lost relatives still rake in about $700,000 a year.
So, considering the abundance of people who can lose their guard for a minute and give access to their device or payment info, the scamming industry shows no signs of stopping.
In recent years, the more “sophisticated” scammers have been targeting small businesses in specific. And, businesses are comprised of individuals. One wrong click or password typed in on autopilot… And your business is kaput.

Why do people still fall for these email scams?
Most often, we are just clicking through emails automatically, not realizing that they might look suspicious.
The second reason is that we are being tricked by something that piques our interest or sounds beneficial. For example, seeing ads that say, “Congratulations, you are the 298,428,293rd visitor today, you win an iPhone!“. Or “If you haven’t received a speeding ticket in 5 years, you can claim big prizes!“.
Thirdly, when we are approached by someone of stature, making it sound like we will be in trouble if we don’t do as they say. Examples include emails or even calls related to unpaid bills, social security fraud, etc.
Know your email scams
Here’s a quick run-through of all the most popular phishing scams you should know about, plus an actionable list to avoid them and keep yourself safe.
Legitimate business fakers
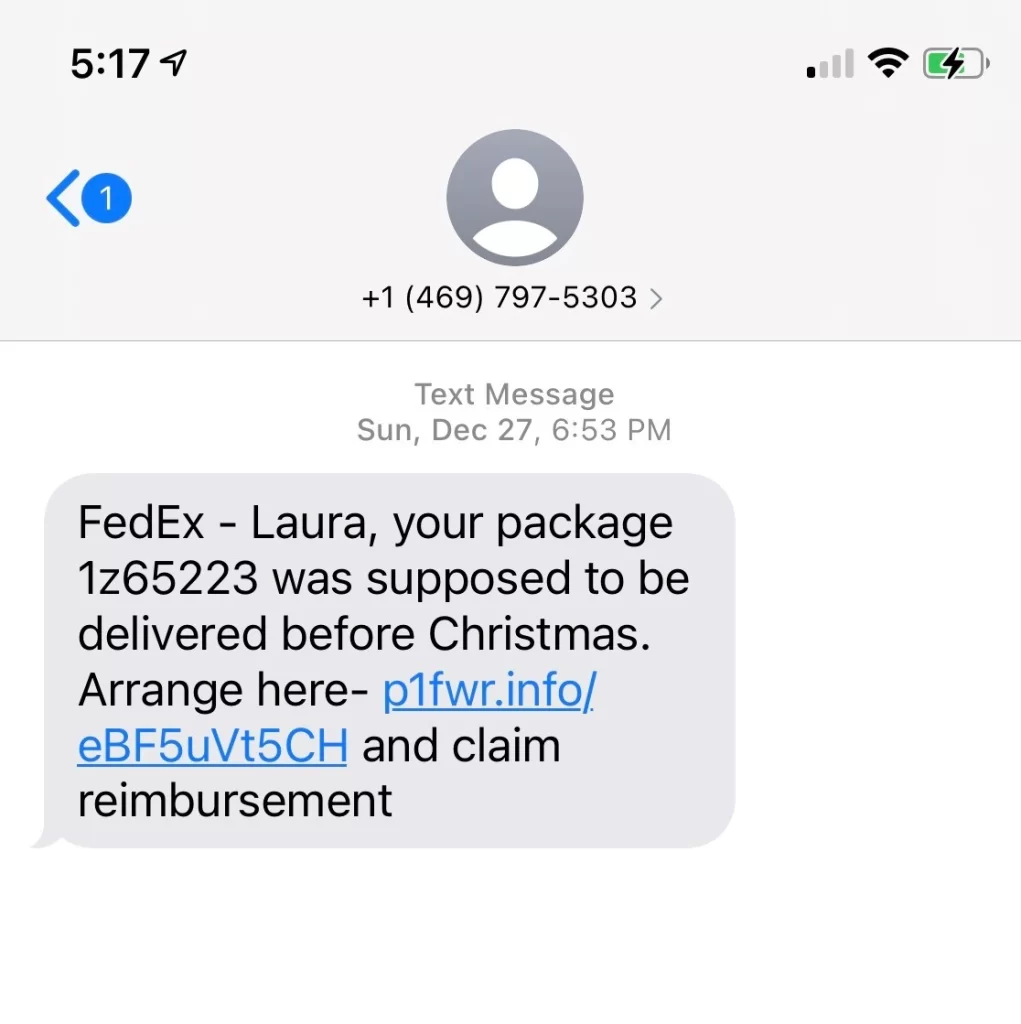
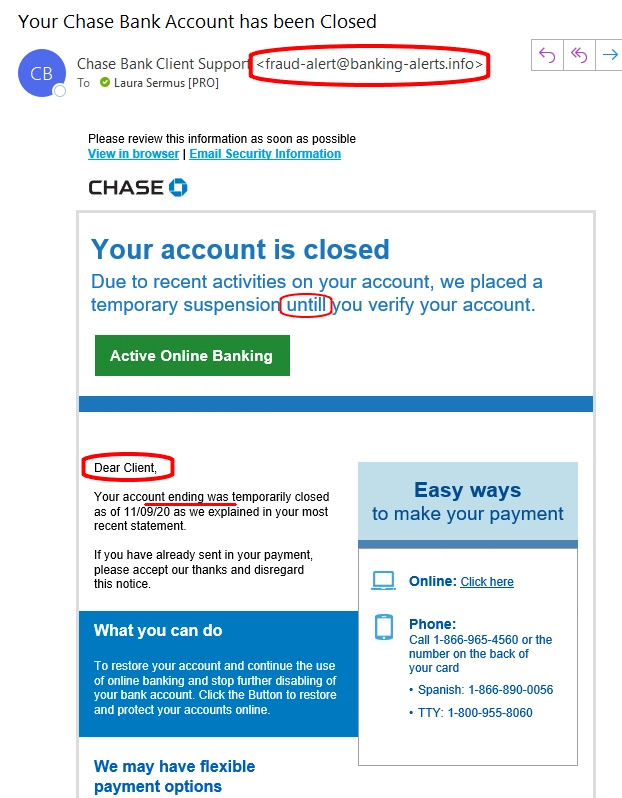
These are simply emails pretending to be real companies, like Microsoft or UPS. They usually ask you to reset your password, check your domain renewal or update your credit card info on “their website.”
How do I avoid this? Use the S-E-A-L method
- Check the Spelling and layout of the email. If the email is coming from a big corporation but looks amateurish (many different fonts, random colors, weird layout) and has some typos, it’s safe to assume it is probably a scam.
- Always check the sender’s Email. It is often similar to the real email, like “microsoft@microsofthelp-usa.com” instead of “o365@microsoft.com”. If it looks suspicious, Google the email and see if it is associated with the real company or not.
- If the email has an Attachment, be extra careful with checking the sender email — even if it’s supposedly sent by a colleague. Attachments can have malware injected into them, so opening them can be risky.
- Hover over Links to see where they direct you. If the email is coming from a reputable source, like your bank, just visit their website yourself and make the required changes, instead of clicking on the link in the email.
Good to know
Sometimes, you don’t even need to give out your personal information to get compromised. In the case of a Reflected XSS Attack, the hackers add malicious code to an email button that will gain access to your browser cookies. Know how sometimes you log into a website, and you’re already logged in?
That’s because cookies save your information to simplify using the company’s services. The hacker will use a weakly secured website to inject their code, then trick you into clicking on their button – taking you to the real site.
However, now equipped with your session cookies, the hacker can log into your account without knowing your credentials.
2. Spear phishing
As the name implies, spear phishing targets one person in specific, instead of sending bulk emails out in the hopes of catching at least a few people. Spearing usually means the attacker has some knowledge of the business hierarchy and knows who they should target. Most businesses have their Teams pages up on their website, so it’s easy to learn the structure.
Examples include emails supposedly sent by the owner or manager, aggressively requesting access to a particular account, or requesting “favors” such as buying gift cards from the store. They could also ask for details about specific projects.
How do I avoid this?
- If the email you received from your boss/colleague seems aggressive or out of the ordinary, call them yourself to verify the request.
- Always double-check the email! Verify that you recognize the full email and don’t just look at the email’s display name.

Protect your business with Protek-IT
- Protek-IT’s monthly phishing simulation email campaign helps train your employees to watch out for scammers.
- The campaign is followed by weekly training, which teaches employees what to look out for and helps them practice their detection skills.
- A report of all the results helps identify pain points and see which employees need more training.
Read more about our Cyber Security projects.



